
by ThinkCode | Sep 8, 2015 | Wordpress
Given Below is some WordPress Security Tips:-
The WordPress platform is one of the fastest, most recognizable Content Management Systems (CMS) available to website owners. It dominates over 23% market share, and has been deployed in large and small organizations alike. With its popularity have come many struggles for website owners; one such struggle is with Security.
1.Use Strong Passwords: The WordPress admin password generated whiling installing time is normally strong so there is nothing wrong with that. Username and password are the heart of your wordpress site dashboard, If password is on lower strength side it may cause into hacking or brutal attacks. So when you installed wordpress then use auto generated password or type strong or lengthy password.
2.Add a CAPTCHA on your WordPress Login: Using a simple captcha to your WordPress login page is another great way to minimize the chance of a bot/script gaining access to your site via a brute force attack.
3.Protect the ‘wp-admin’ Directory: Using .htaccess file protects your wp-admin directory.
4.Update WordPress to the Latest Release: As new WrodPress versions are released the security bugs for previous release becomes public information. WordPress could have vulnerabilities as a result of how the program is written that allow an attacker to pass HTTP arguments, bad URI strings, form input, etc, that could cause Bad Things to happen. So always update your WordPress to the latest version to make sure that you are protected against any known security bugs.
5.Hide WordPress Version: The specific WordPress version that you are using can give the attacker an upper hand in finding a way to break in. So no need to show your wordpress version to other.
6.Backup you’re Data: Always keep backups of all the important files. Take backups of your wordpress
Hope Above WordPress Security tips will help your WordPress sites

by ThinkCode | Sep 7, 2015 | Search Engine Optimization
[easy-tweet tweet=”In SEO, there simply are no short cuts.”] The folks at Google have built an algorithm that is pretty darn difficult to trick and when one does, they fix the loophole quickly. We guess you might see better results from black hat tactics on sites, However, the yearly traffic this website get does not match the monthly traffic of Google.
Black hat SEO is just plain stupid. If someone is willing to just trash a site and start again then it will work. Many internet marketers do this and it does bring results, but a real business should never taint their brand with practices that can earn a Google slap down. Unless you are will to dump your brand, domain and everything and start from scratch you should never do it. But equally it can be just as silly to only follow Google’s webmaster tools Watching black hat marketers will help you find valuable shortcuts for your client. WE use grey hat techniques all the time that bring about great results, but you have to be smart about what you are doing and make sure you are keeping your client safe above all else.
With Google’s most recent algorithm updates, we are understanding that black hat tactics are essentially prehistoric and simply don’t work like they used to. For example, traditional black hat SEO is about loading your site with irrelevant but heavily searched terms, redirects etc. But now not only does onsite search term focus have less of an impact (whether done correctly or not), but also the algorithms are all about building a network around relevancy – incorporating both onsite and offsite search networking methods. The idea is to create an industry leadership around your site, making your brand highly relevant within the industry. Traditional black hat tactics are detrimental to building this leadership and actually work against it in the long run. From what we can tell this trend is only going to strengthen with further updates.

by ThinkCode | Sep 2, 2015 | Search Engine Optimization
There is no such “Right” amount for Google AdWords. It depends on many factors like targeted keywords, audience, goal, CPC of the keywords.
WE would keep in mind the value of your customer/potential client. Use that # as a targeted ad spend for the week/month.
Example: if a mold cleanup company is running Adwords and his average job is about $5,000 then he would use that as a decent ballpark monthly budget. You can certainly break this down to daily, but AdWords takes time so you may be frustrated at first. Also, keep in mind that the more competitive the keyword is, the more you’ll have to pay for visibility. If the ROI isn’t there, you may need to rethink your strategy/ ad platform. (ex, for certain industries, paid social ads may yield better results)
Best thing to do is Determine a budget, or at least an amount they are willing to spend. Determining volumes and rough amounts (CPC) can be done (in part) by using the Adwords Tools section. The Adwords Tools will more or less tell you an expected range that you can spend, but you also have to realize the tool is only as specific as you tell it to be. Many times the volumes and CPCs are merely a loose representation of what should be spent, as it doesn’t always take into account your exact audience.
In the end, we advise our clients, determine a budget and let me build you a campaign to maximize your spend. For instance, I manage a $50k monthly spend for 1 client, but a $2000 spend for another. Both have different audiences, but in each case, I explain what good results are and where we can potentially improve.
Having said all this, spending anything less than $50/day is more or less a waste of resources; even for a very regional company. This is because with $50/day they simply won’t get the recognition (impressions or CTR) they want/expect and it’ll sour the experience for both you and Google Adwords.
At thinkcode, If you are looking for the cheap solution then we are not the right choice, but if you are looking for Best Solution which provides the return on investment, then we would love to help you.
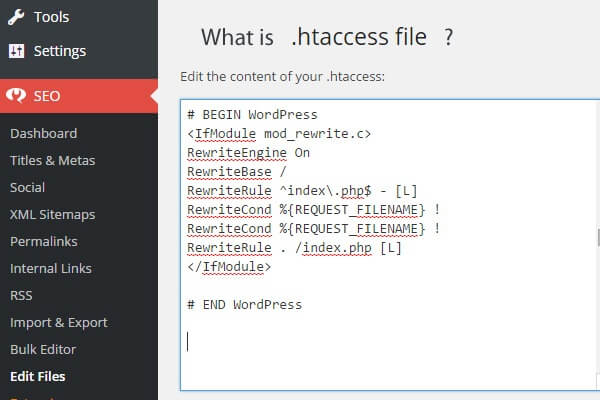
by ThinkCode | Aug 27, 2015 | Woocommerce, Wordpress
Want to know about htaccess file. Check the given below points.
- Htaccess files are configuration files used in Apache web server that controls the directory that it “lives” in–as well as all the subdirectories underneath that directory.
- They are used to override the main web server configuration for a particular directory.
- For .htaccess files to work, the main Apache web server configuration option Allow Override must be enabled.
- If the Allow Override option is not switched on, then the .htaccess file configurations will not work and the main web server configuration will be applied.
- So before applying any configuration changes using .htaccess files always check that they allow Override option is enabled.
- The user must have appropriate file permissions to access and/or edit the .htaccess file. Further, .htaccess file permissions should never allow world write access — a secure permissions setting is “644”, which allows universal read access and user-only write access. Finally, .htaccess rules apply to the parent directory and all subdirectories. Thus to apply configuration rules to an entire website, place the .htaccess file in the root directory of the site.
- Features: .htaccess file include the ability to password protect folders, ban users or allow users using IP addresses, stop directory listings, redirect users to another page or directory automatically, create and use custom error pages, change the way files with certain extensions are utilized, or even use a different file as the index file by specifying the file extension or specific file.
- NOTE:.This file are very powerful and the slightest syntax error, such as forgetting a ‘<’ character, might break the functionality of your website. Therefore before making any changes to an existing .htaccess file always make a backup first. Once you apply the changes test your website thoroughly.

by ThinkCode | Aug 27, 2015 | Wordpress
Given below is Character Definitions for htaccess
- #: the # instructs the server to ignore the line. used for including comments. each line of comments requires it’s own #. when including comments, it is good practice to use only letters, numbers, dashes, and underscores. this practice will help eliminate/avoid potential server parsing errors.
- [F]: Forbidden: instructs the server to return a 403 Forbidden to the client.
- [L]: Last rule: instructs the server to stop rewriting after the preceding directive is processed.
- [N]: Next: instructs Apache to rerun the rewrite rule until all rewriting directives have been achieved.
- [G]: Gone: instructs the server to deliver Gone (no longer exists) status message.
- [P]:Proxy: instructs server to handle requests by mod_proxy
- [C]: Chain: instructs server to chain the current rule with the previous rule.
- [R]: Redirect: instructs Apache to issue a redirect, causing the browser to request the rewritten/modified URL.
- [NC]: No Case: defines any associated argument as case-insensitive. i.e., “NC” = “No Case”.
- [PT]: Pass Through: instructs mod_rewrite to pass the rewritten URL back to Apache for further processing.
- [OR]: Or specifies a logical “or” that ties two expressions together such that either one proving true will cause the associated rule to be applied.
- [NE]: No Escape: instructs the server to parse output without escaping characters.
- [NS]: No Sub request: instructs the server to skip the directive if internal sub-request.
- [QSA]: Append Query String: directs server to add the query string to the end of the expression (URL).
- [S=x]: Skip instructs the server to skip the next “x” number of rules if a match is detected.
- [E=variable:value]: Environmental Variable: instructs the server to set the environmental variable “variable” to “value”.
- [T=MIME-type]: Mime Type: declares the mime type of the target resource.
- []: specifies a character class, in which any character within the brackets will be a match. e.g., [xyz] will match an x, y, or z.
- [] +: character class in which any combination of items within the brackets will be a match. e.g., [xyz]+ will match any number of x’s, y’s, z’s, or any combination of these characters.
- [^]: specifies not within a character class. e.g., [^xyz] will match any character that is neither x, y, nor z.
- [a-z]: a dash (-) between two characters within a character class ([]) denotes the range of characters between them. e.g., [a-zA-Z] matches all lowercase and uppercase letters from a to z.
- a{n}:specifies an exact number, n, of the preceding character. e.g., x{3} matches exactly three x’s.
- a{n,}:specifies n or more of the preceding character. e.g., x{3,} matches three or more x’s.
- a{n,m}:specifies a range of numbers, between n and m, of the preceding character. e.g., x{3,7} matches three, four, five, six, or seven x’s.
- (): used to group characters together, thereby considering them as a single unit. e.g., (perishable)? press will match press, with or without the perishable prefix.
- ^: denotes the beginning of a regex (regex = regular expression) test string. i.e., begin argument with the proceeding character.
- $: denotes the end of a regex (regex = regular expression) test string. i.e., end argument with the previous character.
- ? : declares as optional the preceding character. e.g., monzas? will match monza or monzas, while mon(za)? will match either mon or monza. i.e., x? matches zero or one of x.
- ! : declares negation. e.g., “!string” matches everything except “string”.
- . : A dot (or period) indicates any single arbitrary character.
- –: instructs “not to” rewrite the URL, as in “…domain.com.* – [F]”.
- +: matches one or more of the preceding character. e.g., G+ matches one or more G’s, while “+” will match one or more characters of any kind.
- *: matches zero or more of the preceding character. e.g., use “.*” as a wildcard.
- |: declares a logical “or” operator. for example, (x|y) matches x or y.
- :escapes special characters ( ^ $ ! . * | ). e.g., use “.” to indicate/escape a literal dot.
- .:indicates a literal dot (escaped).
- /*: zero or more slashes.
- .*: zero or more arbitrary characters.
- ^$: defines an empty string.
- ^.*$: the standard pattern for matching everything.
- [^/.]: defines one character that is neither a slash nor a dot.
- [^/.]+: defines any number of characters which contains neither slash nor dot.
- http://:this is a literal statement — in this case, the literal character string, “http://”.
- ^domain.*: defines a string that begins with the term “domain”, which then may be proceeded by any number of any characters.
- ^domain.com$: defines the exact string “domain.com”.
- -d:tests if string is an existing directory
- -f:tests if string is an existing file
- -s:tests if file in test string has a non-zero value















